Jellyfish Explained
The Cyber Security Command and Control Platform
The Jellyfish Factory
With Cogito Group’s Jellyfish, organisations can achieve precision control over vulnerabilities. The holistic interface aggregates numerous security services and products to provide full Credential Management alongside Identity and Access Management.
What is Jellyfish?
Jellyfish® is an innovative cyber security platform offering single pane of glass visibility. It unifies existing architectures to create a secure ecosystem across your organisation, and as your security requirements grow, Jellyfish evolves, future-proofing your organisation.
Single Pane of Glass
Jellyfish is a fully integrated Cyber Security Command and Control System that gives you a number of base security services all in one single glass pane. One interface connects disparate components such as IdaM, PKI, OTP, SSO, Password Management, LACS, PACS, LDAP, DB, MDM, Monitoring and Audit.
Full Credential, Identity, and Access Management
Jellyfish creates granular visibility through its single pane of glass interface. Organisations are given the tools they need to make better access control decisions and spot vulnerabilities. The aggregation of Identity and Access Management and full Credential Management in Jellyfish addresses mission-critical needs regarding access, and provides organisations with the secure resources needed for agility undertaking new initiatives.
Modular, Agile, and Integrated
Jellyfish is purpose-built to handle complexity. Designed as an integrated, cohesive stack, it can evolve with your security requirements. Each module is created with connectivity and emerging technologies in mind. Jellyfish is the ultimate agile cyber-security platform.
About Jellyfish
Jellyfish is the ultimate agile cyber-security platform. Designed to evolve with you, Jellyfish uses future-focused technology to close the gaps in your security architecture. Jellyfish mitigates risks and improves auditing and compliance.
Jellyfish creates a symbiotic ecosystem across disparate systems, evolving with your organisational needs. Jellyfish can integrate legacy systems, BYO applications, devices, users, and credentials. This provides cross-organisational visibility with granular control.
Jellyfish provides the secure resources for agility and control decisions.
Jellyfish Features
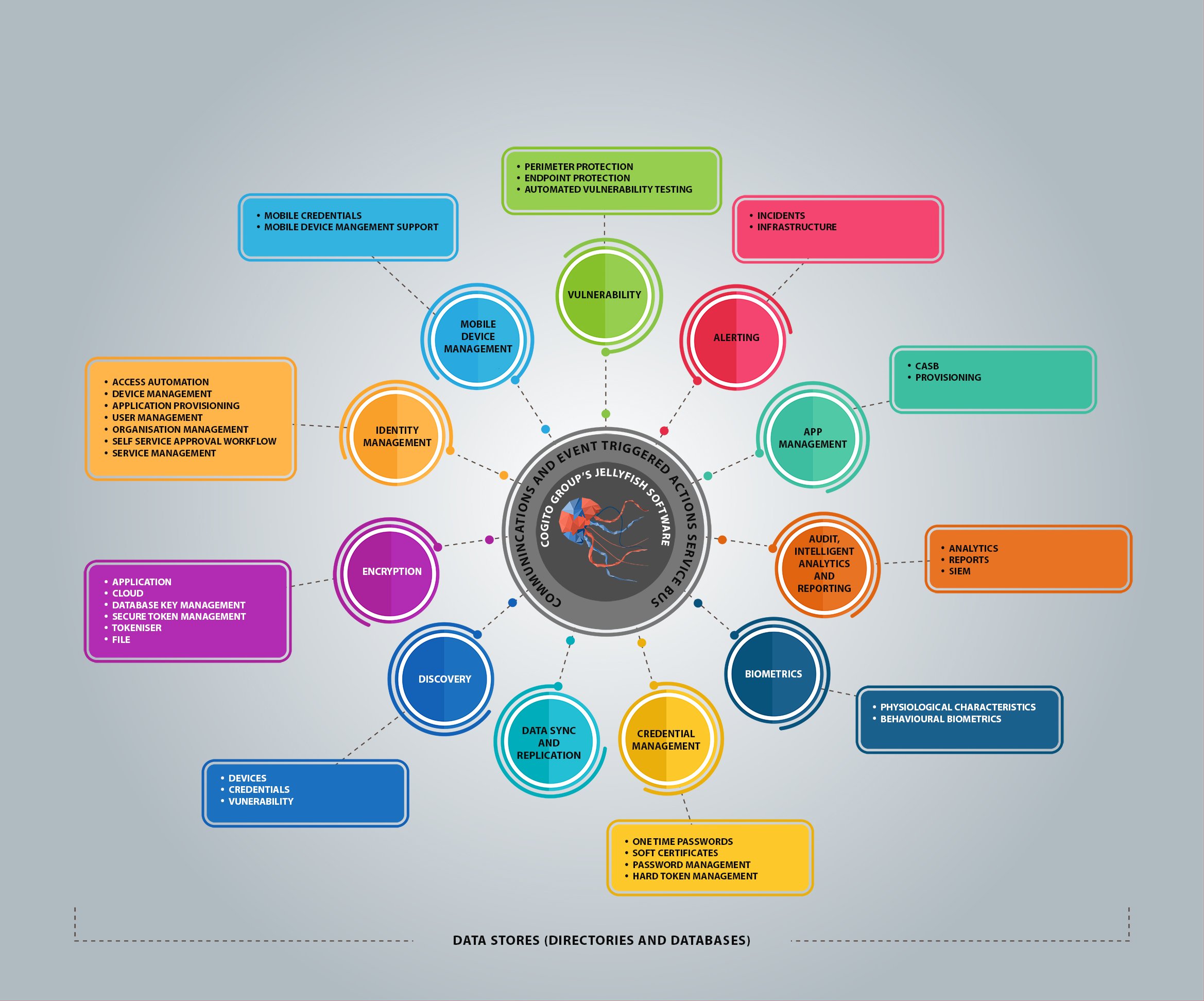
What You Get
Jellyfish provides the most innovative and comprehensive set of requirements enabling security, privacy, confidentiality, integrity, and availability of all information.
Identity Management
- Provide strong authentication to ensure users accessing your network are who they claim to be
- Network authentication
- Digital signatures
- Full identity lifecycle management
Access Management
- Integrated Physical and Logical Access
- Web-based Access to services
- HR workflow – access to workflow
- Access Management based on the known and assured identity
Mobile Device Management
- Remotely manage the entire lifecycle of a device
- Online authentication with a convenient single ID password
Credential Management
- Manage associations between an identity and their issued credentials
- Manage Lifecycle of trusted tokens
- Management of virtual smart cards and credentials to smartphones and other mobile devices
Protected Data Store
- Provides key management
- Transparent encryption of structured, sensitive data residing in:
- Databases
- Files
- File Systems
- Storage Units
Other Features
- Advanced protection to data
- Sophisticated monitoring services
- Mature auditing services
- Comprehensive reporting and analytics functionality
- Integration with internal directories and databases
- Integration with legacy systems
Jellyfish Benefits
Jellyfish is responsive. It provides organisations with an access control system that adapts to changes in organisational architecture and personnel flow. The integration of these services reduces the exposure to risks related to access, responsive provisioning and de-provisioning. Jellyfish provides system monitoring and integration of physical and logical measures. This ensures enterprise efficiency and security.

Take Advantage of New Technology
New devices and software
Jellyfish uses the latest in cyber technology to eliminate vulnerabilities and deliver the highest quality service to our clients.
Developing encryption and security protocols
Jellyfish provides protection and encryption for data in transit and at rest.
Enhanced support for new threat protection
Jellyfish is a dynamic platform that watches for new and evolving threats.
Advances in cloud security protection
Traditional security tools cannot optimally protect an organisations data in the cloud. Jellyfish stays ahead of the curve on cloud security.
Enhanced authentication and identity solutions
Jellyfish creates seamless and airtight identity authentication.

Improved Security
Seamless secure authentication
Jellyfish allows for multiple types of credentials and automates the provisioning and deprovisioning process.
Manage all your credentials in one place
Monitoring
Jellyfish monitors for new and evolving threats to your organisation.
Enhanced device authentication translation
Greater dynamic context decisions
More effective relationship management
Improved data
Systems are able to:
- Share data across systems seamlessly.
- Leverage contextual information for dynamic decision making.
- Leverage relationships for better sharing and decision making

Improved Efficiencies
Automation of tasks
Provisioning and deprovisioning of apps and accounts occurs automatically.
Reduction of adminstration burden
The automation of administration tasks reduces the workload on system administrators.
Cost reduction
Human capital and physical capital required to manage access rights reduces significantly, resulting in a fall in costs.
Automation of changes across your network
Devices across your entire organisational infrastructure communicate with each other, therefore changes apply automatically.
Self-service
Add and remove resources from a single point across multiple applications and services.
Modular architechture
Purchase and plug-in modules you need, only pay for what you need!
Works with existing systems
Extend the life of existing systems without reducing capability.
Replace multiple systems
Replace backend systems at any time.
Seamless transition
Choose new solutions without affecting users.
The Challenges

Technical Landscape is one of Change

Growth in Connection to Digital Services

Growth in Mobile Devices

Access to Data Day and Night From Anywhere in the World
Our Solution is Jellyfish










