How Jellyfish Works
The Jellyfish Platform
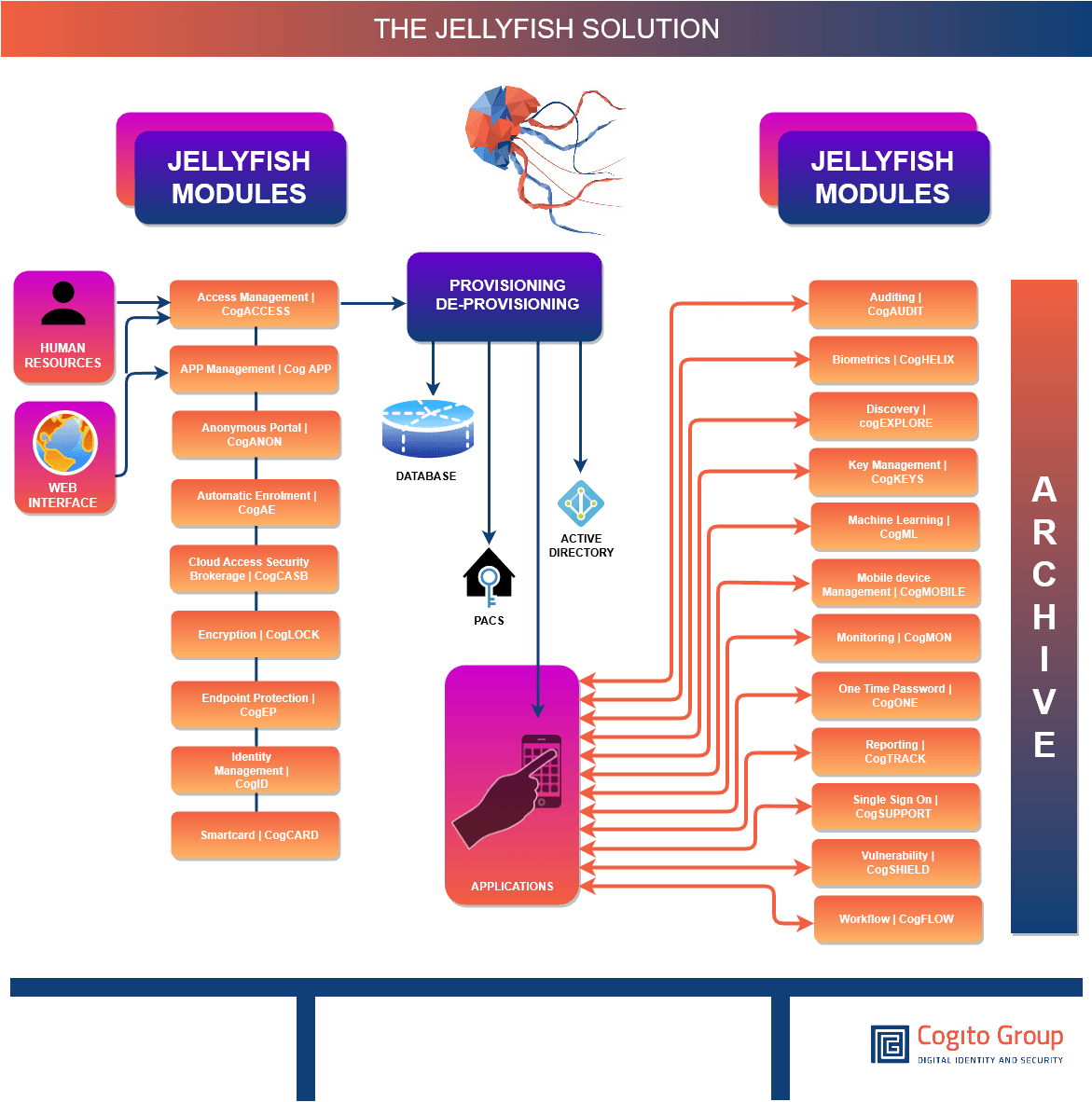
Modular Solution
Jellyfish has been developed as a modular solution. We have significantly improved the way identity, credentials, access, and other security products are managed by developing a series of connectors (Cognectors).
Cognectors
These connectors enable the creation of automatic workflows, pass data through disparate systems and use triggers on one platform (example PACS) to affect another (example LACS).
Service Bus
The Cognectors feed data from disparate systems into the Service Bus. This enables a number of benefits including enhanced monitoring and reporting of activity.
Jellyfish Provides a Single Access Interface for:

Access Management
Access to systems and building areas can seamlessly be added and removed as people join, move within, or leave an organisation through existing HR functions.
Jellyfish uses modern authentication protocols and adaptive support to provide integration with logical and physical access control systems. Jellyfish focuses on future-proofing security, using emerging standards and multi-factor authentication.

Cloud Access Security Brokerage Elements
Data Loss Prevention (DLP), Shadow IT discovery, TLS Decryption, Intrusion Detection System and Intrusion Prevention System (IDS/IPS), Sanctioned IT usage, Analytics, User and Entity Behaviour Analytics (UEBA), Key Management & Data Privacy, Centralised Key Management Services, Bring Your Own Key (BYOK), Hold Your Own Key (HYOK).

Identity Management
Jellyfish uses CRUD management to create secure roles across enterprises. Through data transformation between source and target systems, users are given a trusted identity and granted the access they need to complete the job they have.

Mobile Device Management
Using Jellyfish, administrators can manage Mobile Enterprise and BYOD from within the system, as well as utilise these devices in secure multifactor authentication.

Networking Management
Jellyfish’s networking management capabilities include network devices and firewalls, providing a birds eye view of network connections.

Credential Management
Jellyfish’s credential management capabilities provide administrators with the ability to issue and manage certificates, smartcards, and OTP tokens. Credential management automates the provisioning and access processes for staff as they come, leave, and change roles within an organisation.
Technical Specifications
These are the minimum requirements you will need to use Jellyfish.
Small Deployment
Server OS: Windows Server
Server Type: Virtual Machine
CPU: 6 Cores
RAM: 8GB
Hard Drive: 500GB
Medium Deployment
Server OS:
Windows Server or CentOS Server for CAs
Windows Server or CentOS 7 for other components
Server Type: Virtual Machine
CPU: 24 Cores
RAM: 64GB
Hard Drive: 4TB
Large Deployment
Server OS: Size dependent. See Cogito
Server Type: Virtual or Physical
CPU: Size dependent. See Cogito
RAM: Size dependent. See Cogito
Hard Drive: Size dependent. See Cogito









