How Jellyfish Works
Jellyfish has been developed as a modular solution. We have significantly improved the way identity, credentials, access, and other security products are managed by developing a series of connectors (Cognectors).
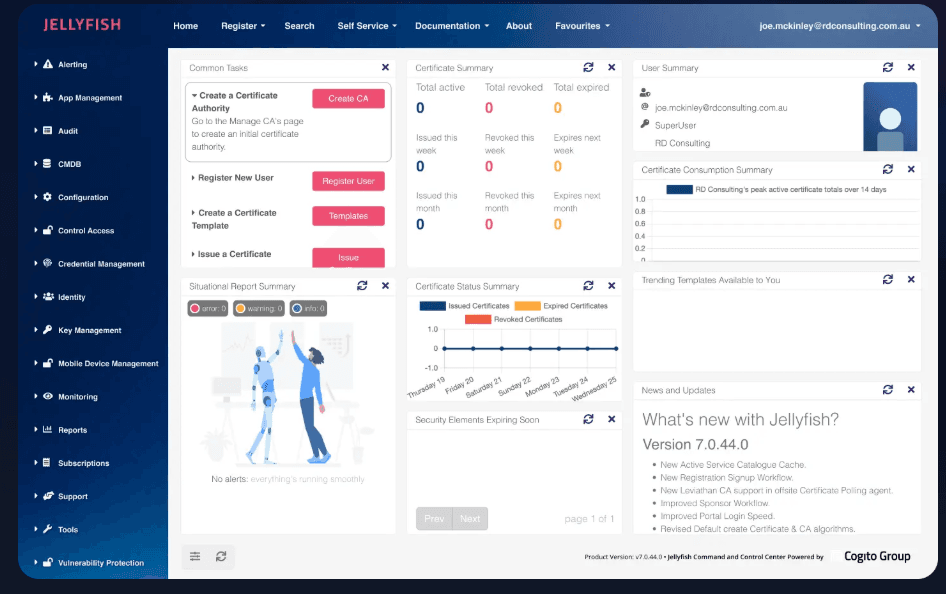
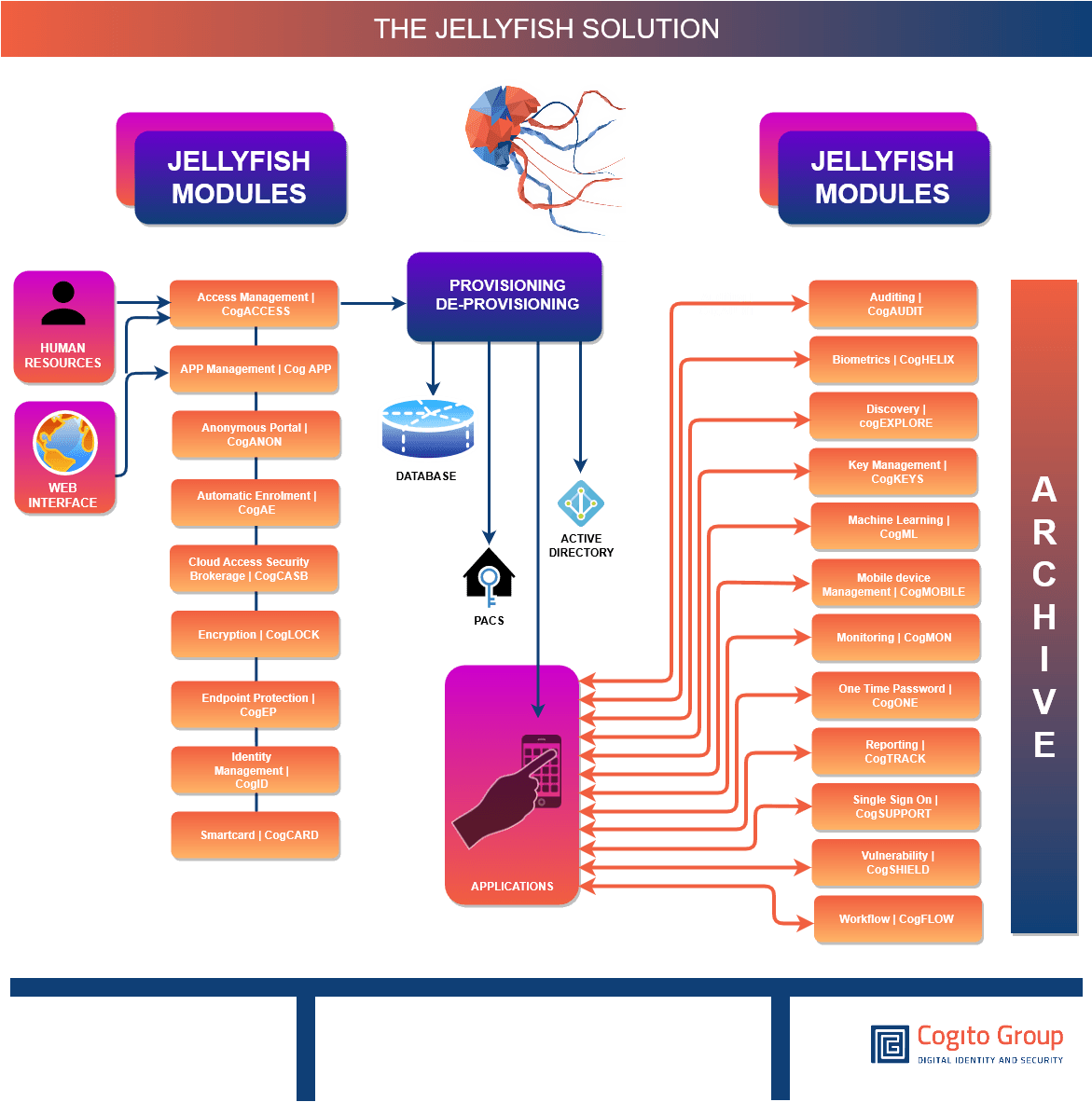
Technical Specifications.
These are the minimum requirements you will need to use Jellyfish.
Small Deployment
Server OS: Windows Server
Server Type: Virtual Machine
CPU: 6 Cores
RAM: 8GB
Hard Drive: 500GBServer OS: Windows Server
Server Type: Virtual Machine
CPU: 6 Cores
RAM: 8GB
Hard Drive: 500GB
Medium Deployment
Server OS:
Windows Server or CentOS Server for CAs
Windows Server or CentOS 7 for other components
Server Type: Virtual Machine
CPU: 24 Cores
RAM: 64GB
Hard Drive: 4TB
Large Deployment
Server OS: Size dependent.
Server Type: Virtual or Physical
CPU: Size dependent.
RAM: Size dependent.
Hard Drive: Size dependent.
Get to know the Jellyfish Training Academy
A dedicated resource designed to help you understand the platform and operate the solution effectively.
