Get to know Jellyfish
A simple, cost-effective, low-risk, complete solution for connecting identities such as users, devices, and services to each other. Jellyfish is a complete and integrated cyber security platform.
.svg)
The Challenge
Today’s technological landscape is one of permanent change. While connections to digital services and mobile devices grow, securing the data generated by those connections is a challenge to manage. Managing it all in one place and sharing this data across siloed systems presents a challenge and an opportunity to do more with less.
Our systems are no longer just on our physical premises, but in the cloud and accessible via the internet, accessed by many devices anytime from anywhere in the world. They are accessed not only by employees but contractors, customers, and partners. Controlling and monitoring access to data is crucial.
To balance security, usability and cost effectiveness, Cogito Group has developed a customisable modular approach. This allows components to be added or removed dependent on an organisations’ individual requirements.
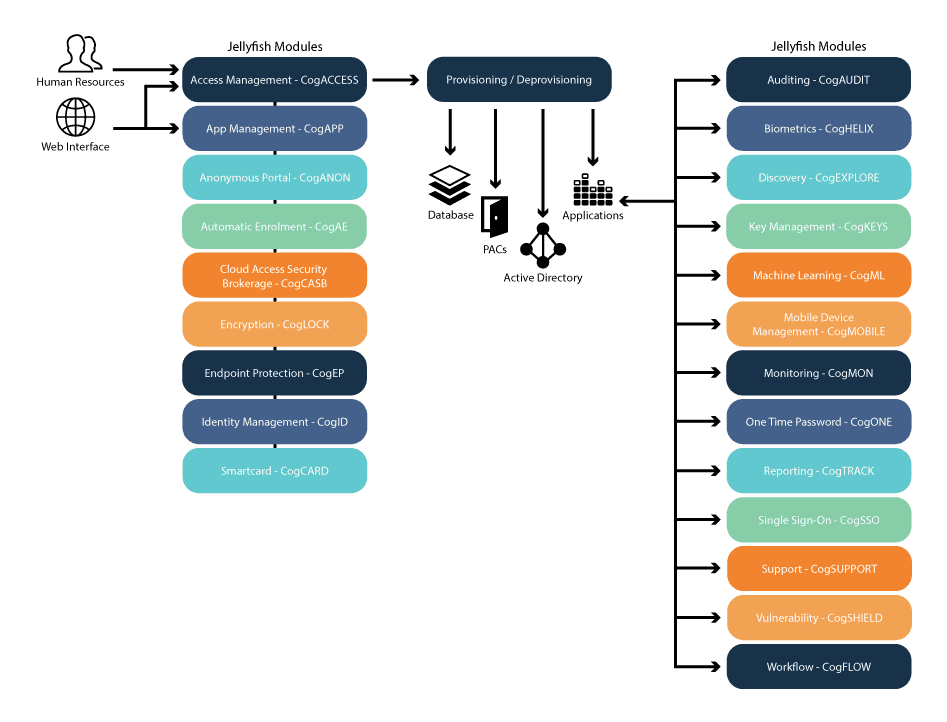
Introducing Jellyfish
Join 5000+ business and Government entities that already use Jellyfish for critical functions, such as increasing security and streamlining business processes around authentication and digital signing. The Jellyfish solution is designed to simplify the creation and management of digital credentials.
Jellyfish enhances your security through increased visibility, greater control, stronger protection, and seamless authentication. Jellyfish is a simple, cost-effective, low-risk, complete solution for connecting identities such as users, devices, services and credentials to each other. Jellyfish allows for enhanced security, better visibility, and simplified and central control. You can improve end-user productivity through seamless authentication, digital signing and automation of processes and changes, reducing your administrative burden.
Uses include those in Finance, Healthcare, Education, Defence, and Legal businesses. Really anywhere you need to manage, protect or use credential types like digital certificates, one-time passwords, electronic keys, passwords or even passkeys. Uses include everything from digitally signing documents and code, to securing websites or internet communications as well as securely authenticating to a service or system.
Jellyfish is available as a service via SecureSME or as installed software on your site or preferred cloud service. It can act as a simple point solution or as an as a service component for your users, devices and systems even when installed on your site.
Core Principles
- Increased visibility across identities, devices, credentials, and certificates
- Consistent access controls for logical and physical environments
- End-to-end automation to minimise human error and outages
- Strong cryptography anchored in hardware security modules (HSMs)
- Open integrations with existing IT, security, and cloud systems
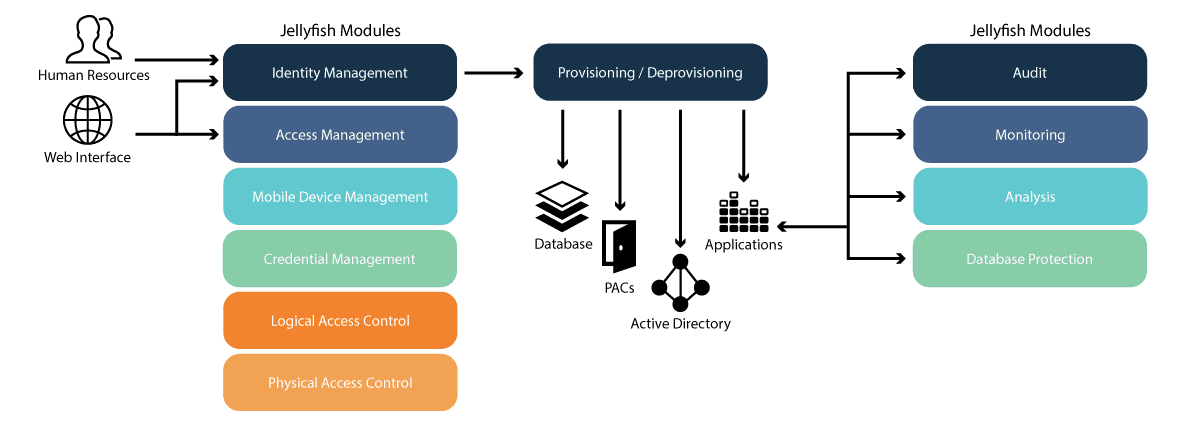
The New Security Foundation
Trust is the basis for every digital interaction. Logging in, opening a secure door, presenting a server certificate, or signing a document. Jellyfish provides that foundation by linking verifiable identities to trusted devices and cryptographic credentials. The result is simple and enforceable, the right people, on trusted devices, obtain the right access at the right time.
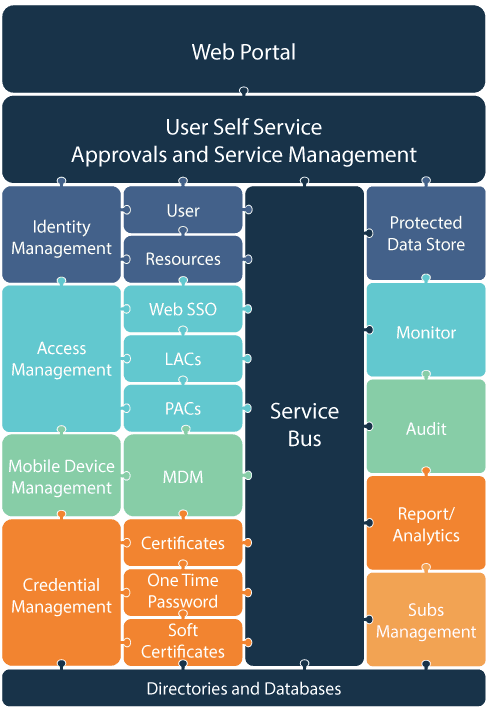
Platform Overview
Identity Management (IdM)
Centralises user lifecycle and governance across employees, contractors, and service accounts. Supports SSO, MFA, role-based and attribute-based access control, and directory synchronisation to keep entitlements accurate as people join, move, and leave.
Certificate Lifecycle Management & PKI
Discovers, issues, renews, and revokes certificates across mixed environments and certificate authorities. Automates enrolment through standards such as ACME, SCEP and AEX. Enforces cryptographic policy and maintains continuous trust with OCSP/CRLs and comprehensive audit trails.

Credential & Smartcard Management
Manages issuance and lifecycle for smartcards and mobile credentials used for logical (LACS) and physical (PACS) access, secure login, and digital signing. Enables personalisation, PIN management, suspension, and revocation from a single interface.

Device Management (DM)
Associate devices with identities, provisions device certificates, and enforces certificate-based network access (e.g., 802.1X/EAP-TLS, VPN). Maintains current inventory and keeps endpoints compliant through automated workflows and policy.
Cryptographic Services
Delivers high-assurance key generation, storage, and operations with HSM protection and policy-enforced algorithms. Supports key wrapping and bring-your-own-key models to align with regulatory and sovereignty requirements.
Monitoring, Reporting & Audit
Provides real-time status, event notifications, and tamper-evident logging. Exposes rich APIs and webhooks for SIEM/SOAR integration and automated service management.
How it Works
- Establish trust anchors: Integrate Directories, CAs, HSMs, PACS/LACS, and Cloud services.
- Automate lifecycles: Enrol, Issue, Rotate, Renew, and Revoke credentials and certificates with policy.
- Enforce access: Apply identity and device-based controls across networks, applications, and facilities.
- Observe & improve: Monitor compliance, receive alerts, and feed telemetry to existing SIEM.
Integrations
Jellyfish connects with commonly deployed enterprise systems to accelerate time-to-value:
Security, Reliability & Scale
- Security by design: Least-privilege services, mutual TLS, strong cryptographic defaults, and policy-driven key management.
- Hardware-backed assurance: Private keys protected in HSMs with support for FIPS-validated components.
- High availability: Resilient microservices, health checks, and data protection with fast recovery.
- Interfaces for builders: REST APIs and Webhooks for integration into DevOps and enterprise workflows.
All models deliver the same capability set, enabling consistent policy and operations.
Deployment Options
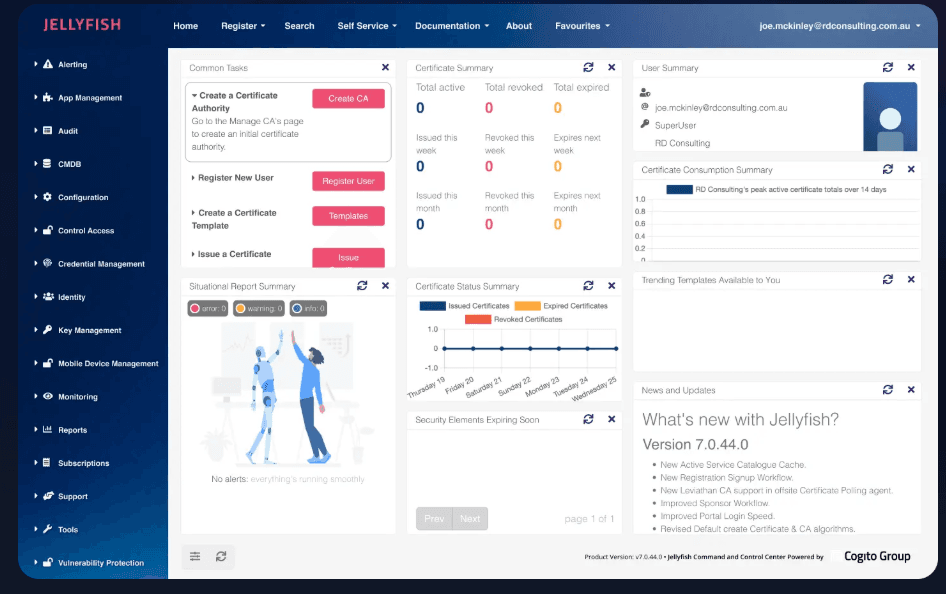
Get to know the Jellyfish Training Academy
A dedicated resource designed to help you understand the platform and operate the solution effectively.