Convergence of PACS and LACS
Physical access control systems (PACS) and Logical Access Control Systems (LACS)
.svg)
Convergence of PACS and LACS
Our digital world has evolved into an ecosystem, with a need to protect the chain of trust via converged credentials. Our access control systems are no longer only physical. Users can access systems from many different devices, day or night from anywhere in the world.
Jellyfish not only elevates how you manage current security components, it also enhances future security capabilities. The convergence of systems creates a scalable infrastructure which grows with devices, networks and most importantly: People.
Access Control Systems
Access control and event monitoring systems provide an additional layer of network security. Implementing an Access Control System within your organisation improves governance and compliance capabilities. With Jellyfish this is achieved at the organisational level and this provides oversight to all other levels.
Cogito Access Control
Cogito’s flagship Access Control System, Jellyfish provides modular layers of cross-organisational security. Jellyfish has been designed with organisational complexity in mind, and built to unify existing architectures to create a secure ecosystem across your organisation.
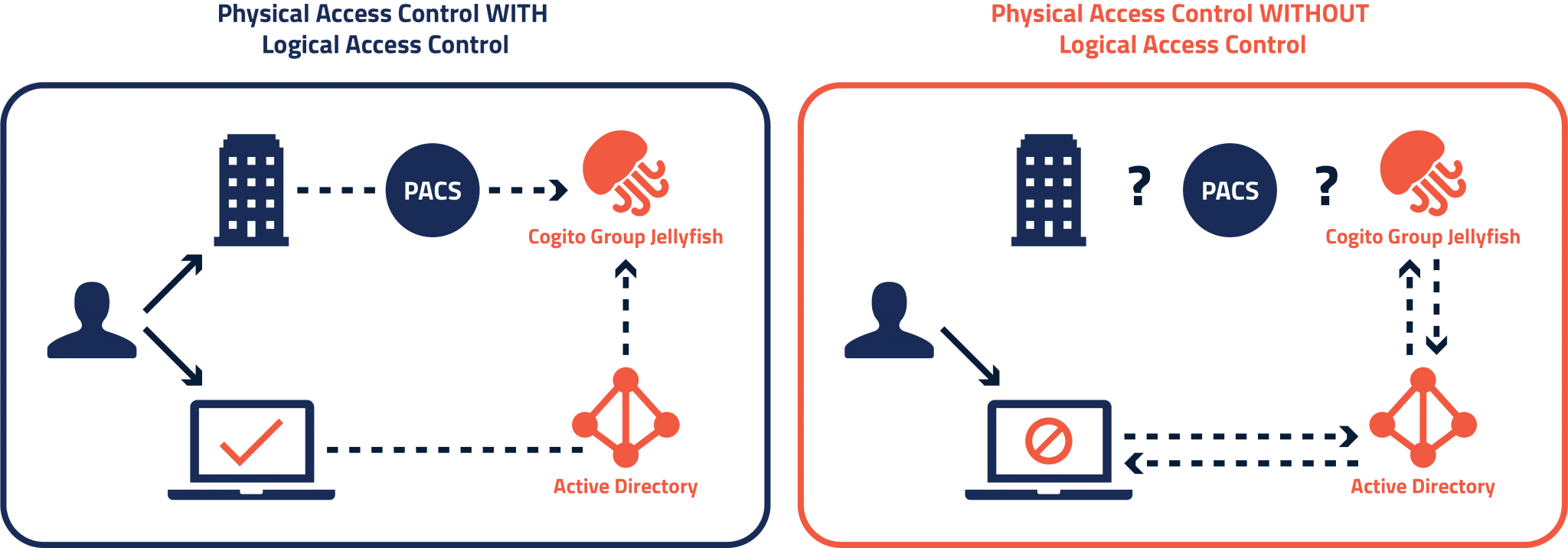
Scenario 1
Your physical access card communicates with the card reader on the door, the door reader then tells your computer (logical) that you have entered the office premise and allows you to logon to your device. In this scenario the entire office environment has gone through a security check, and you’re good to go.
Scenario 2
Your physical access card has not registered against the door reader. Jellyfish detects unusual activity and locks any potential unauthorised device access. The complexities of creating this secure environment, which acts in real-time are all contained in Jellyfish.
The Jellyfish Solution
Jellyfish allows a conversation between multiple protection applications by sending dynamic triggers which allow one system to respond when unusual activity occurs in another system. Jellyfish uses sensor fusion to detect and respond before a breach occurs.
Layers of Security with Just One Tool
Cogito Group’s Jellyfish is a complete and integrated cyber security platform, which:
- Offers the cost benefits of a cloud service
- Improves productivity of resources
- Improves transparency through monitoring, auditing, reporting of security breaches
- Highly scalable through a customised modular approach
- Automated workflows
- Reduced management efforts