Secure Socket Layer (SSL) and Transport Layer Security (TLS)
SSL and TLS are cryptographic protocols. They provide authentication and data encryption between servers, machines, and applications operating over a network.

High Level Benefits

Enables Secure Internet Connection

Safeguards Sensitive Data Between Systems

Prevent Criminals From Accessing Information

Ensure Data Transferred is Unreadable

Use Encryption Algorithms to Scramble Data

Protect Sensitive or Personal Data
Why is TLS important?
Most data transmitted over the internet is unencrypted. This means sensitive information can be easily monitored and tracked by unknown third parties.
This includes:
- Login Details
- Credit Card Details
- Email Correspondence
- Personal Details
- Browsing Habits
- Conference Calls
By enabling and ensuring your client and server applications support TLS, it ensures that data transmitted between them is encrypted with secure algorithms and not viewable by third parties.
For complete security, it is necessary to use it in conjunction with a publicly trusted X.509 Public Key Infrastructure (PKI) in order to authenticate that a system to which a connection is being made is indeed what it claims to be.
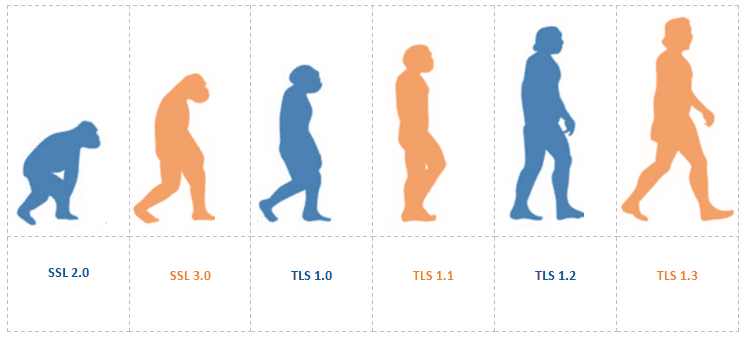
Evolution of SSL and TLS
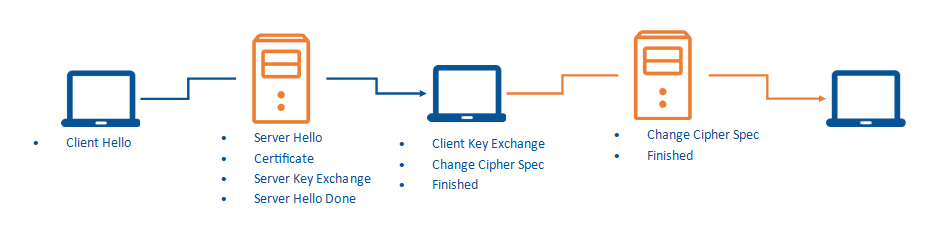
How does it work?
TLS uses a combination of symmetric and asymmetric cryptography.
Symmetric cryptography: data is encrypted and decrypted with a secret key known to both sender and recipient. Symmetric cryptography is efficient in terms of computation, but having a common secret key means it needs to be shared in a secure manner.
Asymmetric cryptography: uses key pairs – a public key, and a private key. The public key is mathematically related to the private key, but given sufficient key length, it is computationally impractical to derive the private key from the public key. This allows the public key of the recipient to be used by the sender to encrypt the data they wish to send to them, but that data can only be decrypted with the private key of the recipient.
The advantage of asymmetric cryptography is that the process of sharing encryption keys does not have to be secure, but the mathematical relationship between public and private keys means that much larger key sizes are required.
TLS uses asymmetric cryptography for securely generating and exchanging a session key. The session key is used for encrypting the data transmitted by one party, and for decrypting the data received at the other end. Once the session is over, the session key is discarded.
With TLS it is desirable that a client connecting to a server is able to validate ownership of the server’s public key. This is normally undertaken using an X.509 digital certificate issued by a trusted third party known as a Certificate Authority (CA) which asserts the authenticity of the public key.